Difference between revisions of "Hostek infrastructure"
| Line 4: | Line 4: | ||
==Bandwidth providers== | ==Bandwidth providers== | ||
| − | Hostek.com utilizes multiple Internet bandwidth providers. By utilizing multiple vendors for Internet bandwidth, service to the hostek.com network avoids interruption from vendor maintenance and outages. See | + | Hostek.com utilizes multiple Internet bandwidth providers. By utilizing multiple vendors for Internet bandwidth, service to the hostek.com network avoids interruption from vendor maintenance and outages. See image below. |
| − | [[File: | + | [[File:Bw_providers.png|link=|Internet bandwidth providers]] |
| − | + | ||
| − | + | ||
==Server and storage hardware== | ==Server and storage hardware== | ||
| − | Hostek.com is proud to utilize Dell servers and Dell Compellent | + | Hostek.com is proud to utilize Dell servers and Dell Compellent storage arrays. |
==Server virtualization with high availability== | ==Server virtualization with high availability== | ||
| Line 21: | Line 19: | ||
Another added benefit to virtualization is that resources such as CPU, RAM, and disk space, can be quickly allocated based on utilization patterns. This ensures optimal performance for your site or mail server with minimal down time. | Another added benefit to virtualization is that resources such as CPU, RAM, and disk space, can be quickly allocated based on utilization patterns. This ensures optimal performance for your site or mail server with minimal down time. | ||
| − | |||
| − | |||
==Redundant power== | ==Redundant power== | ||
| Line 30: | Line 26: | ||
==Storage== | ==Storage== | ||
| − | Virtual machines, along with their data (i.e. your web site files, email, etc.) reside on enterprise | + | Virtual machines, along with their data (i.e. your web site files, email, etc.) reside on enterprise SAN arrays. These arrays have the following features: |
| − | * | + | |
| + | *Disks configured in high performance RAID configurations for redundancy | ||
*Redundant storage controllers | *Redundant storage controllers | ||
| − | |||
*Redundant network adapters | *Redundant network adapters | ||
| − | *Redundant storage | + | *Redundant storage networking switches |
*Redundant power supplies connected to redundant power feeds | *Redundant power supplies connected to redundant power feeds | ||
*All servers are connected to the storage network via multiple paths for performance and redundancy | *All servers are connected to the storage network via multiple paths for performance and redundancy | ||
| − | + | All SAN volumes are cross replicated to disparate SAN each day. In the event of failure on one SAN array, replicated data can be access on the second SAN array and vice versa. | |
| + | <!--Additionally, all data on our storage arrays are replicated to standby storage devices daily. This means that should an array cluster fail, the replica can quickly be brought online to resume storage. See figure 2 below for an example of normal operations. Figure 3 is an example of a storage array failover situation. Note that in the failover situation, "Data volume 1" and "Data volume 2" become available on the standby array and virtual machines depending on those volumes may resume normal operations.--> | ||
| − | |||
| − | |||
| + | [[File:Storage_Diagram.png|link=|figure 2]] | ||
| − | |||
| − | |||
| + | |||
| + | <!--[[File:san-failover.png|link=|figure 3]] | ||
| + | '''figure 3''' -- failover situation--> | ||
==IT security== | ==IT security== | ||
| Line 55: | Line 52: | ||
===Firewall & IPS=== | ===Firewall & IPS=== | ||
| − | Perimeter firewall and Intrusion Prevention System (IPS) | + | Perimeter firewall and Intrusion Prevention System (IPS) with the following features: |
| + | *Highly available for redundancy | ||
*Stateful packet inspection | *Stateful packet inspection | ||
*Deep packet inspection for known malicious attack patterns | *Deep packet inspection for known malicious attack patterns | ||
*DDoS (Distributed Denial of Service) protection mechanisms | *DDoS (Distributed Denial of Service) protection mechanisms | ||
| − | |||
| − | |||
===SPAM filtering=== | ===SPAM filtering=== | ||
Revision as of 23:28, 7 May 2018
A significant amount of effort and expense goes into designing and maintaining the network infrastructure to ensure maximum performance and availability of services hosted by hostek.com. Below are some of the highlights of the hostek.com infrastructure.
Contents
Bandwidth providers
Hostek.com utilizes multiple Internet bandwidth providers. By utilizing multiple vendors for Internet bandwidth, service to the hostek.com network avoids interruption from vendor maintenance and outages. See image below.
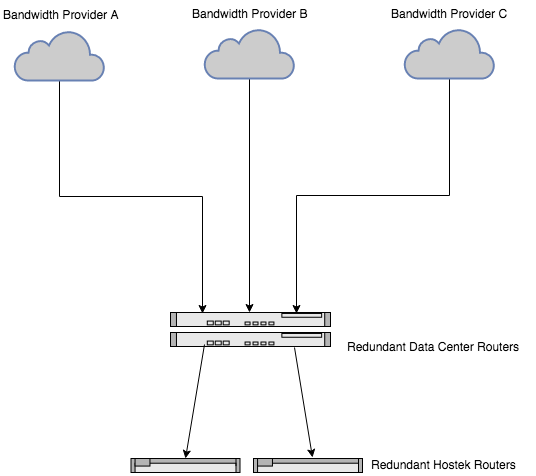
Server and storage hardware
Hostek.com is proud to utilize Dell servers and Dell Compellent storage arrays.
Server virtualization with high availability
Our web servers are virtualized utilizing VMWare vSphere. With VMWare High Availability, should a physical server fail, any virtual machine will be automatically migrated to another physical server and powered on, and resume normal operations. This operation can be completed with the affected virtual machines back in service often in 3-5 minutes! This is an amazingly short time frame to recover from a failed physical server.
Another added benefit to virtualization is that resources such as CPU, RAM, and disk space, can be quickly allocated based on utilization patterns. This ensures optimal performance for your site or mail server with minimal down time.
Redundant power
Electricity is provided from two separate power feeds. In addition, our equipment is protected with UPS systems and diesel generators. Servers and storage devices have redundant power supplies, each on separate feeds to help prevent loss of data due to power failures.
Storage
Virtual machines, along with their data (i.e. your web site files, email, etc.) reside on enterprise SAN arrays. These arrays have the following features:
- Disks configured in high performance RAID configurations for redundancy
- Redundant storage controllers
- Redundant network adapters
- Redundant storage networking switches
- Redundant power supplies connected to redundant power feeds
- All servers are connected to the storage network via multiple paths for performance and redundancy
All SAN volumes are cross replicated to disparate SAN each day. In the event of failure on one SAN array, replicated data can be access on the second SAN array and vice versa.
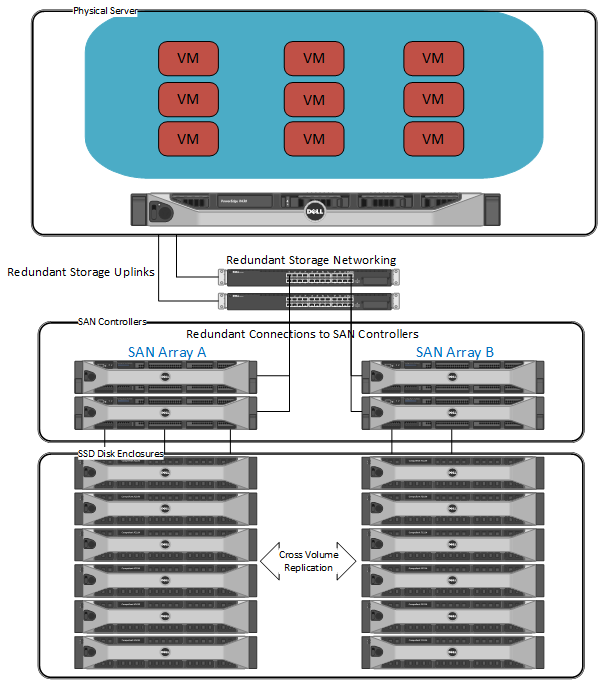
IT security
- Note This section is not a comprehensive guide to our IT security. This just serves to highlight some of the general points.
Firewall & IPS
Perimeter firewall and Intrusion Prevention System (IPS) with the following features:
- Highly available for redundancy
- Stateful packet inspection
- Deep packet inspection for known malicious attack patterns
- DDoS (Distributed Denial of Service) protection mechanisms
SPAM filtering
All inbound email is filtered using multiple real-time RBL and content inspection technologies.
Additionally, outbound mail from our Windows web servers are checked with anti-SPAM content filters to prevent delivery of mail from your site from being disrupted by compromised mail submission forms from other tenants on the server your site resides on.
Anti-virus
Our servers run commercial anti-virus products from reputable software vendors.
Backups
For our Shared and Reseller customers, we perform daily backups of all web, email, and database servers. For VPS customers, we backup the full virtual machine if a Nightly Backup option is selected. We strongly recommend for VPS customers to choose a backup option.
Backups for VPSs are stored off-site in most cases in a location that is in a different geographical area than the primary site. This means that should a major disaster occur in the area where the servers running your VPS reside, your data is safe in another location.
Physical security
Restricted access to premises
The buildings housing our datacenter have a comprehensive security system which include but not limited to the following:
- 24x7 on-site security
- Access codes
- Biometric hand scanners
- Electronic proximity readers
- Security surveillance system
Fire suppression system
Our equipment is protected by a pre-action, dry pipe fire suppression system.
PCI Compliance
Click here for details on hostek.com's PCI Compliance.